The world runs on code and ciphers. From your private conversations to online transactions, cryptography is involved in almost everything you do digitally. In fact, life, as we know today, would not be possible without it.
Cryptography is the science of secret communication where the aim is to transfer the information over an insecure channel in such a way that no third party can understand what is being conveyed. Security has become a critical issue as the Internet is providing new ways to gain access to systems and data. Every connected device is an endpoint, acting as a potential back door for hackers.
Even if you don’t have millions to lose, protecting what you do have matters a lot. There are many different types of security technology available, but encryption is the one that every digital device user should know. We have tried to explain the most common encryption methods that are currently used to save your private information.
Before we start: you should know every encryption method uses a key to turn a plain text message into ciphertext. There are two basic types of encryption –
- Symmetric (secret key): Uses the same key for both encryption and decryption.
- Asymmetric (public key): Uses different keys for encryption and decryption.
Table of Contents
8. Triple DES

Triple DES was developed to replace the original DES algorithm (Data Encryption Standard) algorithm. Actually, the DES was using 56 bits key size that later became vulnerable to brute force attacks because of increased computational power.
Triple DES provides a simple method to expand the key size of DES (by applying DES algorithm thrice to each data block), without the need to develop a completely new block cipher algorithm. The total key length adds up to 168 bits. Because of the meet-in-the-middle attack (MITM), the effective security it provides is only 112 bits.
Microsoft’s Outlook, OneNote, and System Center Configuration Manager 2012 use Triple DES to protect user content and system data. It is also used in many electronic payment industries and other financial services.
7. Blowfish

Yet another symmetric key algorithm designed to replace DES. It is known for its effectiveness and speed. It is placed in the public domain, which means anyone can use it for free.
Blowfish works with a 64-bit block length and a variable key size, ranging between 32 bits to 448 bits. The encryption involves 16 round Feistel cipher, using large key-dependent S-boxes.
On the downside, it is vulnerable to birthday attacks, especially in contexts like HTTPS. It is recommended that you shouldn’t use Blowfish to encrypt files larger than 4 GB due to its small 64-bit block size.
Blowfish can be found in dozens of software categories, including database security, eCommerce platform, file and disk encryption, password management and archiving tools, steganography, file transfer, secure shell, and email encryption.
6. AES

AES (Advanced Encryption Standard) is the successor of DES and trusted as the standard by the United States government and various organizations. Low RAM requirement and high speed were the main reason it was selected to hide top-secret information. The algorithm can perform well on a wide range of hardware, from 8-bit smart cards to high-performance processors.
Although AES is extremely efficient in 128-bit form, it also uses keys of 192 and 256 bits for heavy security. It has 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys. The same key is used for both encryption and decryption of data.
To date, no practical attacks against AES have been discovered. It is used in many different protocols and transmission technologies, such as WPA2 protection of WiFi network, Voice-over-IP technology, and signaling data.
Read: What Is AES Encryption? Working | Performance | Security
5. Twofish
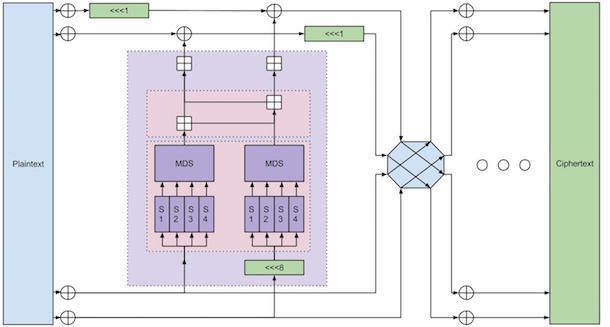
Computer security professional Bruce Schneier is the mastermind behind Blowfish and its successor Twofish. The algorithm has a Feistel structure like DES and employs a Maximum Distance Separable matrix.
Twofish is a symmetric key encryption method that uses 128-bit block size and key size up to 256 bits. One half of the n-bit key is used as an encryption key and the other half is used to modify the encryption algorithm (key-dependent S-boxes). It is slightly slower than AES but somewhat faster for 256-bit keys.
The algorithm is flexible – it can be used in network apps where keys are changed frequently, and in systems where only a small amount of RAM and ROM is available for use. You will find it bundled in encryption tools like GPG, TrueCrypt, and PhotoEncrypt.
4. RSA
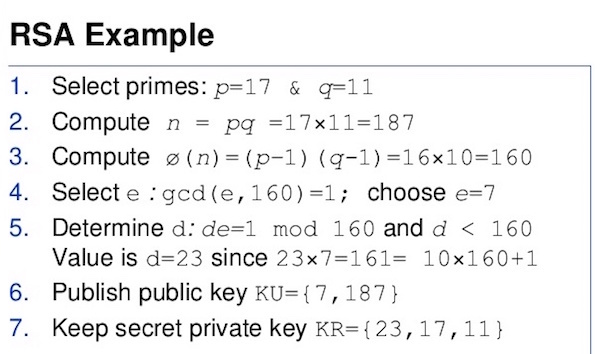
RSA is an asymmetric key encryption technique and a standard for encrypting data sent over the Internet. In this approach, the encryption key differs from the decryption key, which is kept private. The asymmetry depends on the practical difficulty of factoring the product of two large prime numbers.
The strength of encryption increases exponentially with the increase in key size, which is typically 1024 or 2048 bits long. While implementing, RSA must be combined with some sort of padding scheme so that no message results in insecure ciphertexts.
RSA is not governed by any active patents; anyone can use it. It can perform encryption, decryption, and signature verification, all with the same two functions. The only downside of using public-key cryptography for encryption is speed. Also, it might be vulnerable to impersonation, even if the user’s private keys are not available.
Read: 15 Notable Hacker Groups and their Famous Hacks of All Time
3. Diffie-Hellman Key Exchange

Also known as Exponential Key Exchange, Diffie-Hellman is a public key cryptography technique followed shortly after RSA. It lets two parties with no prior knowledge of each other jointly establish a shared secret key over an insecure channel.
The limitation of this algorithm is the lack of authentication. Data using Diffie-Hellman are vulnerable to man-in-the-middle attacks. It is well suited for use in data communication, but less often used for data archived/stored over a long period of time.
This public domain algorithm is used to secure a wide range of Internet services. It provides the basis for multiple authenticated protocols and is used to provide forward secrecy in Transport Layer Security’s ephemeral modes.
Read: 12+ Biggest Software Failures Of All Time
2. ElGamal Encryption

ElGamal encryption is asymmetric key cryptography based on the Diffie-Hellman Key Exchange. Its security depends on the difficulty of computing discrete logs in a large prime modulus. In this approach, the same plaintext gives a different ciphertext each time it is encrypted. However, the ciphertext generated is twice as long as the plaintext.
The encryption can be defined over any cyclic group, and its security depends on the properties of the underlying group as well as the padding scheme used on the plaintext.
Read: The MegaCollection of Best Hacking Tutorials, Tools and Resources
ElGamal encryption is deployed in recent versions of PGP (Pretty Good Privacy) and GNU Privacy Guard. It is also used in a hybrid cryptosystem, where the plaintext is encrypted using a symmetric cryptosystem, and ElGamal is then used to encrypt the key.
1. ECC
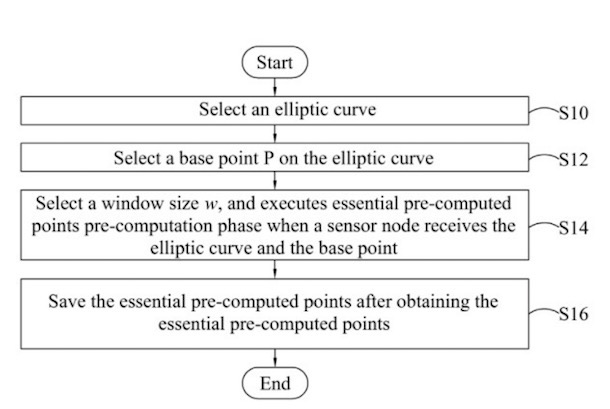
Elliptic Curve Cryptography is an asymmetric encryption method based on the algebraic structure of elliptic curves. Instead of the traditional approach of generating keys as the product of large prime numbers, ECC creates keys through the properties of the elliptic curve equation.
The security of ECC is based on the ability to calculate a point multiplication and the inability to calculate the multiplicand provided the original and product points. Elliptic curve size determines the difficulty level of the problem. It can provide a level of security with a 164-bit key that other systems (like RSA) require a 1024 bit key to achieve. The elliptic curves are applicable for digital signatures, key agreement, and pseudo-random generators.
NSA is the biggest supporter of this technology, and it is being developed as the successor to the RSA approach. In August 2015, NSA announced that they are planning to use Elliptic Curve Diffie-Hellman for key exchange and Elliptic Curve Digital Signature algorithm for digital signature.
Read: 11 Famous Uncracked Code | Mysterious Ciphertexts
Future of Encryption
Cyber attacks and machine’s computational power are constantly evolving, so security experts must stay busy in the lab discovering new schemes to keep them at bay. A team of researchers has found a new method called Honey Encryption that will deter the attackers by serving up fake data for every incorrect attempt of the key code.
Hopefully, this will slow down hackers and bury the original key in a haystack of false hopes.
Then there are emerging techniques like Quantum Key Distribution that shares keys embedded in photons over fiber optics. It might have viability not only at present but many years into the future as well.


