In the good old days, hacking was used to learn information about systems and IT, but now it has taken on a dark connotation. A hacker’s job is quite tougher than a software developer’s job. Even at a beginner level, a hacker requires to have depth knowledge of multiple topics. First of all, you must know Assembly language, Bash scripting, C, Python, PHP (for web applications) programming languages. You can’t exploit a system or program if you don’t know how code is written in these languages works.
Along with the knowledge, you must have passion and positive attitude towards complex problem-solving. The new security software (with better protection than previous) are constantly evolving, therefore you must keep learning new things at a really fast pace.
The article is for all those who are thinking about ethical hacking as a career option. We’ve gathered a few free tutorials followed by tools and resources that will help you speed up on your learning. These tools are just to help you get started or make your job a little bit easier. All the listed resources are for educational purposes only.
Remember: No tool can make you a hacker. You have to find the vulnerability(s) and exploit the program yourself.
Table of Contents
Hacking for Dummies – Tutorials

Let’s start with level 1. These tutorials are not as simple as they sound. To understand them better, you need to acquire operating system concepts, networking basics and programming fundamentals.
Dumbest Ideas in Computer Security: It will show you the 6 anti-good ideas which come from inappropriate attempts to do the impossible. These six points will make ASIC-based turbo-stateful packet-mulching firewall transparent to you.
The OWASP Guides: Learn how to perform specific activity that contributes to the app security. There are multiple articles focused on specific topic and are full of information about how to perform application security tasks.
Introduction to Penetration Testing: Learn what is penetration test, what are vulnerabilities, security research, exploit and what is payload, explained in simple English.
Backtrack Penetration Testing: This is penetration testing tutorial using Backtrack Linux. The results of the testing are addressing the vulnerabilities in the system as well as particular recommendations for fixing those vulnerabilities.
Information Gathering with Nmap: This is a basic walk-through of a penetration test. The tutorial focuses on finding live hosts on the network, port scanning and software versions running on those ports.
Tutorials Related to Cryptography
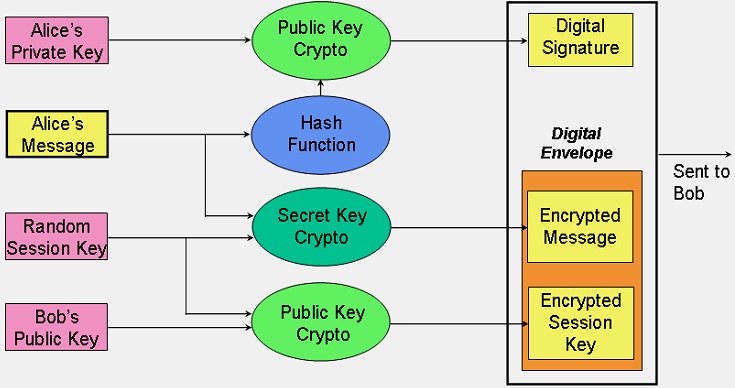
Cryptography is a technique of storing and sending data in a specific form so that no third party can read or change it. For example, techniques like merging words with images, replacing characters with digits etc. As per the modern methods, cryptography is associated with scrambling plaintext into ciphertext (called encryption) and then ciphertext to plaintext (called decryption). Overall, learning cryptography involves a deep understanding of mathematics.
An Overview of Cryptography: This paper has two main purposes: The first is to explain some of the important term and concept behind basic cryptography method and the second is to provide some real examples of cryptography in use today.
Introduction to Public-Key Cryptography: Learn what exactly cryptography is and how data is transferred in a secure way. Here you’ll learn types and uses of certificates, how they are used to establish trust, managing and issuing certificates and more.
Herong’s Tutorial Examples: This cryptography tutorial book includes information about certificate, cipher, DES, keytool, blowfish, MD5, PEM, RSA, SHA, SSL, PKCS#8, PKCS#12 and other commonly used encryption techniques.
Godzilla Crypto Tutorial: This is a high level tutorial that contains 973 slides in 12 parts. It covers encryption protocol, algorithms and mechanisms, key management and certificates, digital signature legislation, authentication and much more.
Read: 10 Most Notorious Hackers
Databases Vulnerability
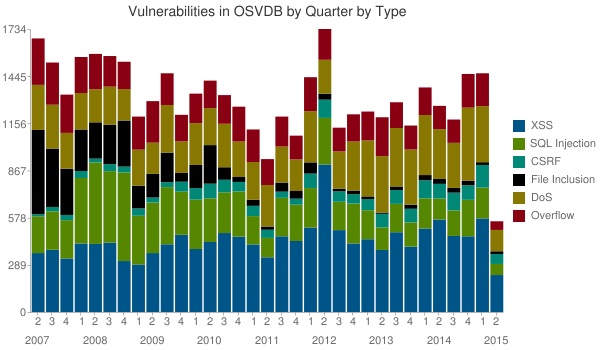
As we all know, the database is a big source of information for attackers to understand the system and exploit, avoid or fix vulnerability. Any new vulnerability detection is usually available through the public vulnerability databases. This is the key factor and should be in the first place to start your day as a security professional.
Exploit-DB: This is the ultimate archive of exploits, security papers and Shellcode. Overall, a great resource for penetration testers, vulnerability researchers and security addicts alike.
SecurityVulns: This is one of the leading Russian information security related resources. Here you can find news, advisories, software and exploits.
1337day: The aim is to collect exploits from submittals and various mailing lists and merge them in one easy-to-navigate database.
Red Hat Security Alerts: The page contains advisories for all products served by the Red Hat Network including certificate system, cloudforms, developer toolset, JBoss web server, network proxy and network satellite.
Linux Security Repository: It offers various security related resources including vulnerability database, security alert database and weekly edition security page.
Security Focus: It provides all security related details, from original news content to detailed technical paper and guest columnists. The vulnerability database section is packed with the latest information on vulnerabilities for all platforms and services.
Microsoft Security Bulletin: All Microsoft vulnerabilities and news are published on second Tuesday of each month.
Zerodayinitiative: This is a list (from 2005 to date) of all publicly disclosed vulnerabilities discovered by site’s researchers.
OSVDB: This is open sourced vulnerability database that provides accurate, detailed, current and unbiased technical security information.
OVAL: It is Open Vulnerability and Assessment Language that focuses on how to assess and report upon the machine state of computer systems.
National Vulnerability Database: The automating vulnerability management, security measurement and compliance checking system. You can search CVE and CCE vulnerability database.
SecuriTeam: It’s a small group dedicated to presenting you the up-to-date news and utilities in computer security. Explore the new vulnerabilities, testing tools and reviews.
Apache Security Repository: It lists all security problems fixed in the previous Apache version. Apache HTTP Server vulnerabilities are labeled with Common Vulnerabilities and Exposures (CVE) identifiers.
Secunia Advisories: Get the updates on new vulnerabilities of all giant technology industries including Oracle, Microsoft, Google, Apple, IBM and more.
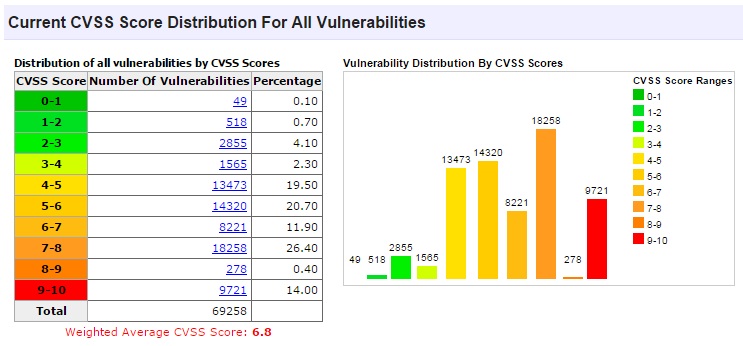
CVE Details: This is ultimate security vulnerability datasource. Here you can generate a custom RSS feed, an embeddable vulnerability list, or a Json API call URL.
Videos and Play Lists

This is for those who prefer video tutorials. The list includes both small and lengthy videos. Feel free to explore more, share or suggest us anything you like.
The Cryptography Course: This tutorial will teach you about the inner working cryptographic primitives and how to apply this knowledge in real world problems and applications.
Cybersecurity and Its Ten Domains: This course will introduce you to the exciting field of cybersecurity. You can engage with videos, participate in knowledge assessments, gain insight from industry experts, learn access control, security architecture, and physical and environmental security.
What happens when you steal a hacker’s computer: A small, brilliant and kind of funny video that will tell you what are the consequences of buying stolen or hacker’s computer.
Open Security Training: A YouTube playlist of more than 90 hours (including 117 videos). They’ll teach you about Intel x86, ARM, trusted computing, software exploits, exploitation in the Windows environment and more.
Nmap- Scanning the Internet: Learn the whole new level of scanning millions of Internet host as a part of worldscan project. The video includes interesting findings and empirical statistics from these scans, as well as practical advice for improving your own scan performance.
Web application Pen testing: Learn bypass authentication, HTTP method, SQL injection, spidering web applications, brute force attacks, Cross site scripting, contrast Nmap and Amap service, how to exploit metasploitable and more.
DEFCON- How I Met Your Girlfriend: A small YouTube playlist for discovery and execution of entirely new classes of web attacks in order to meet your girlfriend. It includes PHP session hijacking, HTML5 client-side XSS, NAT penetration, remote iPhone Google Maps hijacking and finding accurate geo-location data from a web browser.
Websites to Learn Ethical Hacking from Scratch

There are many certified websites out there that teaches you ‘how to become a successful hacker’. You can register there and learn from the level 0. Some of these sites also cover security updates, exploits and tools.
Cybrary: It’s a free online IT and cyber security network that provides easy-to-follow instructions. Here you can learn almost anything related to security including system and network administration, advanced penetration testing and cyber security.
Hackaday: It provides daily hacks, guides, tips and tricks that may interest you. Apart from the design and color, all articles have been clearly categorized.
Hacking-Tutorial: The website publishes some of the great methods to hack network, tweak software, database etc. It also suggests you new online tools and whitepapers related to security.
Latest Hacking News: The website provides the information related to security, especially black and white hacking news. Their aim is to spread awareness among security experts and hackers.
Hacking Tutorials (Android app): The app includes step by step guides that explain various hacking techniques. It shows you how to safely perform a given hack, how it works and how to protect yourself against them.
Read: 10+ Different Types of Computer Viruses
Whitepapers and eBooks

A few research papers and ebooks by experts can provide you a lot of useful information and inspiration. Some of them are really difficult to understand therefore you may need to read them more than once.
Hacking- The Art of Exploration: The book will teach you how to run existing exploit, how hacking techniques actually works, how to write shell scripts, assembly programs, run arbitrary code and more. It is available on Amazon for $17.
10 Deadly Sins of Cyber Security: Cyber security is in response mode and growing in significance. The whitepaper focuses on sins of cyber security. On the same webpage, you can download “5 phases every hacker must follow”.
Network Penetration Testing: This guide reveals how to use penetration testing tools and best practice for performing a penetration test.
Penetration Testing for iPhone/iPad applications: The paper focuses on helping security professionals understand the nuances of penetration testing iPhone and iPad apps. It covers the key step of configuring the proxy tool and decompiling applications.
Handbook of Applied Cryptography: The book contains some free chapters – cryptography overview, public key parameter, hash function, digital signature, key management, efficient implementation and more. The full book is available on Amazon.
How to hack anything in Java: Many applications in the enterprise world feature thick Java clients. Learn possible ways to break those app security parameters.
The collection of Security and Vulnerabilities: This contains the whitepapers from different sources. Here you’ll get all information about security research, vulnerabilities, exploit and testing.
Engineering Principles for Information Technology Security: The paper presents a list of system level security principles to be considered in the design, development & operation of information systems.
Forums for Hackers

Forums are really great help for learning from others. Tons of security experts, ethical and non-ethical hackers share their knowledge on forums, without charging anything.
Do enough research before posting a question and be polite and patient.
Information Security Stack Exchange: This is very popular question and answer site for information security professionals. It’s completely free and you don’t need to register to post a question/answer.
Security Info Watch: Here you can ask any question related to security, just don’t post the question that has been asked before, otherwise you’ll be marked as a spam. The site is for professionals, by professionals, and they intent to keep in that way.
Spyware, Viruses, and Security Forum: This is the best source by CNET for finding the latest news, help and troubleshooting advice from their community experts.
Hack Forums: The site includes 3 sections- premium hacking tutorials, free e-book hacking tutorials and video guides.
Recommended: 15 Worst Computer Viruses of all time | Explained
Hacking and Security Tools

There are dozens of tools available for performing different types of tests and hacking. Some of the very common and useful tools are listed here. Remember, they’ll just help you make your process faster, nothing else.
Nmap: The open source utility for security auditing and network discovery. It uses raw IP packets to determine hosts, services, operating system, packet filters/firewall and other characteristics.
Hping: A command line oriented TCP/IP packet assembler/analyzer. It supports TCP, UDP, ICMP and RAW-IP protocols and has ability to send files between a covered channel.
Wireshark: It’s an open source packed analyzer used for network troubleshooting, software and communication protocol development. The tool is similar to tcpdump, but has front-end plus sorting and filtering options.
Network Security Services: This is set of libraries that support cross-platform development of security enabled clients and server apps. Apps designed with NSS supports PKCS #5, PKCS #7, PKCS #11, PKCS #12, SSL version 1 &2, S/MIME and other security standard.
Nikto: This is a web server scanner that performs comprehensive tests against web servers for various items and also checks for server configuration.
OpenSSH: The free SSH connectivity tool that encrypts all traffic (including password) to eliminate connection hijacking, eavesdropping and other attacks. It provides secure tunneling capabilities and several authentication methods.
Aircrack-ng: This is a set of tools for auditing wireless networks. The 802.11 WEP and WPA-PSK keys cracking program can effectively recover keys once enough data packets have been captured.
GDB: The GNU project debugger allows you to see what’s going on inside another program while it executes and what another program was doing at the moment it crashed.
Metasploit: It is penetration testing software that helps you verify vulnerabilities and manage security assessments. A tool can handle couple of thousand shells at once.
Skipfish: It’s a reconnaissance web application security tool. Some of its features are recursive crawls, dictionary-based probes and cutting-edge security logic.
Sleuth Kit: A collection of command line tools and C library that allows you to analyze disk images (including file systems like FAT, HFS+, UFS, NTFS) and recover files from them.
AIDE: Stands for Advanced Intrusion Detection Environment, a file and directory integrity checker. It supports various message digest algorithms and file attributes.
Splunk: A traffic monitoring software that offers the leading platform for Operational Intelligence. Collect the machine data that are both valuable and usable.
Inspirational Bonus: Who Are Hackers?
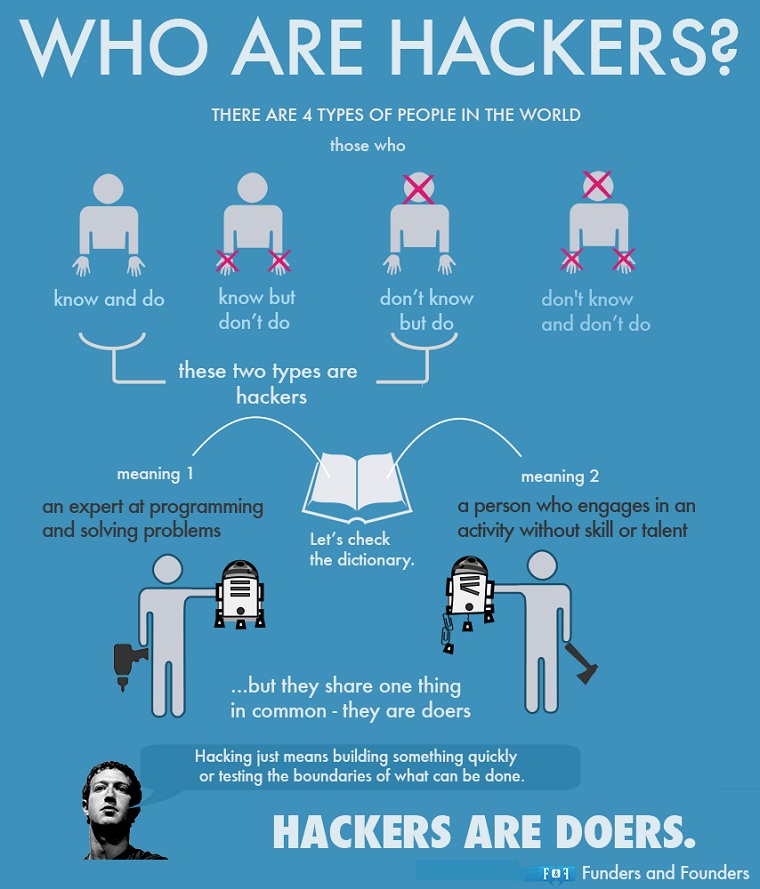 Image credit: fundersandfounders
Image credit: fundersandfounders
Now Read: 15 Notable Hacker Groups and their Famous Hacks of All Time


Thanks for sharing this tools http://www.viralhacks360.com