To understand anti-aliasing, we first need to understand the concept of aliasing. You may have experienced pixelated or jagged edges on your screen while watching videos or playing video games. These ‘jaggies’ are known as aliasing. It...
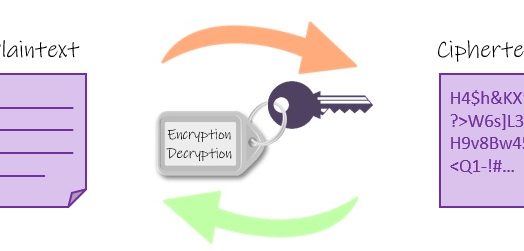
The world runs on code and ciphers. From your private conversations to online transactions, cryptography is involved in almost everything you do digitally. In fact, life, as we know today, would not be possible without it. Cryptography is the...
The hypervisor is a fairly old technology, but it is still super relevant for enabling virtualization. The first hypervisors to provide full virtualization were developed by IBM in 1967. They were developed as a test tool (named SIMMON) for...
The term ‘nanotechnology’ was first coined by Professor Norio Taniguchi in 1974. He was describing semiconductor processes that exhibit characteristic control on the order of a nanometer. How small is one nanometer? The human hair is...
The terms Artificial Intelligence (AI), Machine Learning (ML), and Deep Learning (DL) have become very common these days. They are often used interchangeably, especially while dealing with Big Data, analytics, and searching and indexing. Although...
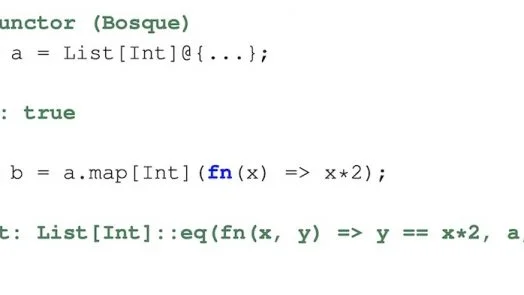
Bosque language aims to improve software quality and enhance programmers’ productivity. It gets rid of sources of complexity like mutable state, reference equality, and loops. It is inspired by TypeScript and JavaScript programming languages...
A New AI model can fabricate talking avatars from a single image. Developers applied this model to popular paintings, including Leonardo Da Vinci and Mona Lisa. The outcomes have some visual glitches, but they are far impressive than previous...
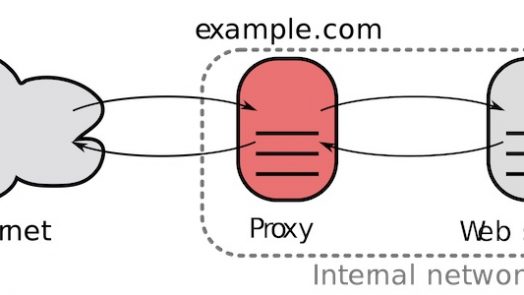
A proxy server acts as a gateway between you and the internet. It hides your real IP address from the resource server, adding an extra layer of privacy. It is mostly used for bypassing filters and censorship. If you have ever been a part of a...
The term haptic is derived from the Greek word “haptikos”, which means a sense of touch. The sense of touch can be categorized as active and passive. Haptic is mostly associated with active touch to communicate or recognize items. It may...
The Advanced Encryption Standard (AES) is currently the most popular and widely adopted symmetric encryption algorithm. It was developed by two Belgian cryptographers, Vincent Rijmen and Joan Daemen. If properly implemented, the algorithm is...
The concept of quantum systems was first proposed by a Russian mathematician, Yuri Manin, in 1980. However, it was Richard Feynman who conceived the possibility of quantum computers in the early 1980s. Feynmann proposed that quantum computers would...
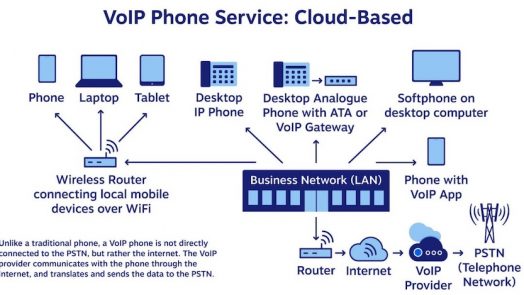
WiFi calling is a service that allows users to make and receive calls over a WiFi network using their existing phone numbers. It is very simple to use, and it doesn’t require any separate application or log-in. Making a WiFi-call on a...