Birthplace of brands such as Sony and Panasonic, Japan is considered one of the world’s most innovative nations. For much of the second half of the 20th century, Japanese tech companies dominated the world with their cutting-edge innovations...
The one thing that makes Android superior to other operating systems is the level of customizability it offers to its users. It even allows you to configure the system files. Its open nature has encouraged a large community of developers to...
The current state of the quantum computing industry is dynamic and promising. According to a study by McKinsey, four sectors — finance, chemical, life sciences, and mobility — are poised to experience the earliest impacts of quantum...
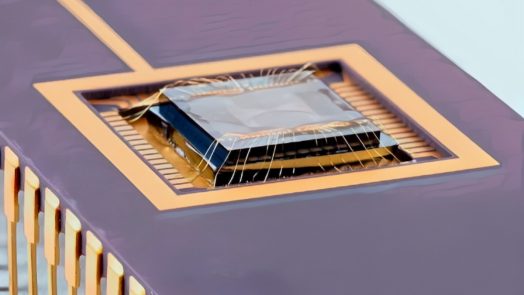
Micro-Electro-Mechanical System, or MEMS, is a miniature device or machine that is made of both mechanical and electrical components, using techniques of microfabrication. The term ‘MEMS’ is often used to describe both a category of...
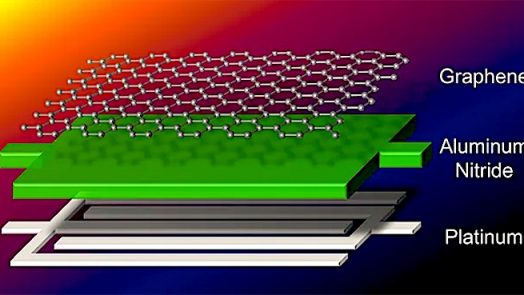
NEMS (short for NanoElectroMechanical System) are devices that integrate electrical and mechanical functionality at the nanoscale, i.e., at or below 100 nanometers. They are the advanced level of miniaturization after MEMS (MicroElectroMechanical...
As demand for energy storage soars, traditional battery technologies face growing scrutiny for their cost, environmental impact, and limitations in energy density. These challenges have fueled a surge of innovation in battery research, driving...
The world of electronics is about to change a lot. Technologies like artificial intelligence and quantum computing are making things more exciting and different. It’s like a fast and thrilling evolution in the world of electronics. Over...
We create more than 2.5 million terabytes of data every day. The total amount of data produced, captured, and consumed globally will increase dramatically, and it is projected to reach over 250 zettabytes in 2027. This data comes from everywhere:...
Battery technology has improved a lot these days. But if there is one thing people will never be able to get enough of it is the promise of prolonged battery life. Wouldn’t it be great if our laptops and smartphones lasted a whole week of...
6G is the sixth-generation wireless technology for digital cellular networks. 6G will utilize the upper limits of the radio spectrum and support 1 Tbps (terabytes per second) speeds. It will bring down the latency of communication to one...
The number of security threats is increasing day by day, making high speed wired/wireless network insecure and unreliable. According to the study conducted at the University of Maryland, hackers attack internet-connected devices every 39 seconds on...
If you are an intense gamer, you may have come across a confusing option in graphics settings. It’s called VSync, and it very hard to guess what it actually does and why this option is provided. Short Description: VSync stands for Vertical...