Okta, a leading cloud-native Identity-as-a-Service (IDaaS) provider, has redefined how companies authenticate users, manage access, and enable Zero Trust security frameworks.
With annual revenue surpassing $2.6 billion and a customer base of over 18,000 enterprises (including FedEx, Zoom, and Nasdaq), Okta has established a formidable presence in both workforce identity and customer identity and access management (CIAM) segments. [1]
At the same time, the identity and access management (IAM) market is projected to grow to $62 billion by 2032, with a compound annual growth rate (CAGR) of 16.1%. This rapid growth is drawing intensified competition from both tech giants and niche players, challenging Okta’s market position. [2]
In fact, IAM is no longer just about Single Sign-On and Multi-Factor Authentication. Modern rivals offer capabilities like identity governance, adaptive authentication, lifecycle management, machine learning-driven risk detection, and passwordless experiences.
Below, I highlight Okta’s leading competitors and alternatives, examining their strategic advantages and how they are challenging Okta in this multi-billion-dollar identity race.
Did you know?According to industry reports, about 4 in 5 data breaches involve weak or stolen credentials, underscoring the critical importance of robust identity protection. [3]

Table of Contents
14. Oracle IDCS
Launched: 2016Core Rivalry: Competes in legacy + cloud hybrid IAM setups
Competitive Edge: Hybrid integration with OCI & Oracle apps
This is a comprehensive Identity-as-a-Service (IDaaS) platform offered by Oracle Corporation. It plays a critical role in securing Oracle Cloud Infrastructure (OCI) as well as third-party applications.
IDCS seamless integration with Oracle’s SaaS offerings (like Oracle ERP, HCM, and SCM) makes it particularly valuable for Oracle-centric enterprises. The platform supports both workforce IAM (for internal users) and consumer IAM (for external users), making it a versatile solution for hybrid identity scenarios.
It also brings conditional access, adaptive security, and centralized policy management into the picture, making it a solid IAM tool for compliance-driven industries.
Oracle has invested heavily in AI and analytics to enhance the capabilities of IDCS. This includes risk-based authentication, behavior-based threat detection, and audit trail capabilities that are vital for governance and compliance.
While it may not be the most nimble IAM solution on the market, its value becomes evident in enterprise-grade, multi-cloud, and hybrid settings. Compared to Okta, which excels in agility and developer appeal, Oracle IDCS delivers in compliance, hybrid enablement, and enterprise consistency. [4]
13. OneLogin
Launched: 2009Number of clients: 5,500+
Core Rivalry: SSO, MFA, & extensive app integrations
Competitive Edge: Speed and ease of deployment
OneLogin offers fast-to-deploy, cloud-first identity security solutions that cater to both small businesses and large global enterprises. ts platform allows organizations to centralize identity, reduce the attack surface, and implement Zero Trust security by managing who has access to what, when, and how.
With over 6,000+ pre-integrated applications, OneLogin accelerates deployment and simplifies administration for IT teams, making it a strong choice for fast-scaling organizations.
OneLogin serves over 5,500 enterprise customers, securing more than 40 million identities globally and processing millions of authentication events through its Trusted Experience Platform. Prominent users include Airbus, Uber, AAA, Steelcase, Stitch Fix, and others across high-tech, finance, and government sectors.
Its key offerings include single sign-on (SSO), user provisioning, adaptive multi-factor authentication (MFA), directory integration, and role-based access control (RBAC).
However, the platform differentiates itself with SmartFactor Authentication, an AI-powered risk engine that adapts authentication flows based on real-time signals such as user behavior and login context.
12. HID Global
Launched: 1991 (Hughes Identification Devices)Number of employees: 4,000+
Core Rivalry: Authentication Service
Competitive Edge: Physical + digital identity convergence
HID Global plays a crucial role in both physical and digital security ecosystems, serving government agencies. financial institutions, educational institutions, and healthcare providers across more than 100 countries.
HID has built a robust portfolio over decades, combining hardware (like smart cards, RFID readers, mobile credentials) with software solutions for identity issuance, management, and authentication. Its products are often used in highly secure environments such as data centers, airports, banks, and corporate campuses.
The company is particularly prominent in government ID programs, supplying identity documents such as ePassports, national ID cards, and driver’s licenses. It also delivers solutions for secure printing, visitor management, and biometric verification (e.g., fingerprint and facial recognition).
As digital transformation accelerates, HID is shifting from legacy proximity cards to mobile access and biometrics. According to its 2025 State of Security & Identity Report, 61% of security leaders cite mobile credentials as a top trend, and 35% already deploy biometrics, with another 13% planning to adopt facial, fingerprint, or iris identification in the near future. [5]
11. JumpCloud

Number of clients: 180,000+
Core Rivalry: All‑in‑one platform for small to mid‑size organizations
Competitive Edge: Identity security for high-risk users, SaaS expansion
JumpCloud unifies user identity, device access, and security controls across heterogeneous IT environments, including Windows, macOS, Linux, and cloud infrastructure.
Its core offering is its Open Directory Platform, which serves as a centralized identity backbone for companies seeking to control and secure user access to various systems, applications, and networks.
Unlike conventional IAM solutions that are often siloed or limited to specific environments, JumpCloud is designed to be platform-agnostic, supporting Google Workspace, Microsoft 365, AWS, VPNs, Wi-Fi, and even legacy systems.
It also provides built-in device management, enabling policy enforcement directly on user endpoints. This makes JumpCloud ideal for IT teams that want a consolidated stack, especially in Mac- or Linux-heavy environments.
10. CyberArk

Number of clients: 8,000+
Core Rivalry: Competes in PAM and workforce IAM
Competitive Edge: Identity security for high-risk users, SaaS expansion
CyberArk has long led the Privileged Access Management (PAM) industry and is now expanding into a comprehensive Identity Security Platform protecting both human and machine identities.
While many IAM vendors cover broader identity access, CyberArk offers deep technical control over privileged credentials, session monitoring, vaulting, and just-in-time access.
In recent years, the company has rapidly embraced SaaS delivery by launching cloud-native versions of its core solutions. It has also strengthened its offerings through strategic acquisitions. The $1.5 billion acquisition of Venafi in 2024 enhanced its machine identity management capabilities, while the acquisition of Zilla Security in 2025 expanded its identity governance and administration (IGA) capabilities. [6][7]
In 2024, CyberArk was named a leader in Gartner’s Magic Quadrant for Privileged Access Management (PAM) for the sixth consecutive year, as well as in KuppingerCole’s Leadership Compass for Secrets Management.
The same year, it launched integration with SentinelOne and Microsoft Defender for Identity and open‑source FuzzyAI tool to guard against AI-model jailbreaks.
9. Transmit Security
Launched: 2014Number of users: 100 million+
Core Rivalry: Passwordless and customer identity market
Competitive Edge: Developer-first, passwordless-first approach to CIAM
Transmit Security is a rapidly growing cybersecurity company that focuses on passwordless authentication, identity orchestration, and customer identity and access management (CIAM).
It delivers an API-first, developer-friendly platform helping enterprises build secure, frictionless login and identity flows. The key offerings include passwordless biometrics, step-up authentication, risk-based access controls, identity verification, and user journey orchestration.
It also provides out-of-the-box integrations with major platforms like AWS Cognito, Azure AD B2C, Salesforce, and Okta, enabling hybrid CIAM strategies.
In 2024, Transmit Security surpassed $100 million in annual recurring revenue (ARR), with 40% YoY revenue growth and a 51% increase in customer base. The platform now supports over 100 million users, including seven of the top ten US banks. [8]
In 2025, the company was featured in the Fortune Cyber 60 list, a prestigious ranking of leading venture-backed cybersecurity innovators.
8. BeyondTrust
Launched: 1985 (as Symark)Number of clients: 20,000+
Core Rivalry: Threat detection across identity attack surfaces
Competitive Edge: Device & OS coverage
BeyondTrust specializes in Privileged Access Management (PAM) and identity-centric security solutions. It helps organizations secure and manage privileged credentials, reduce insider threats, and enforce least privilege principles.
While Okta enables access neutrality and cross-cloud application support, BeyondTrust actively analyzes attack paths, highlighting configurations, stale entitlements, cloud misconfigurations, and privilege escalation risks. Okta focuses on access provisioning and governance, whereas BeyondTrust protects and audits those accesses across the identity surface.
Its Identity Security Insights platform deploys in about 30 minutes, offering visibility across on-prem, cloud, SaaS, and federated environments. Tools like True Privilege expose hidden privilege pathways and prioritize remediation.
In 2023, BeyondTrust surpassed $400 million in annual recurring revenue (ARR), with subscription ARR making up more than 80% of the total. The company reported nearly 40% YoY growth in subscription ARR.
In 2024, BeyondTrust maintained a gross retention rate above 95% and achieved a Net Promoter Score (NPS) of 62, along with a customer satisfaction (CSAT) rating of approximately 95%.
The company continues to receive strong recognition in industry analyst reports, including the Gartner Magic Quadrant for Privileged Access Management (PAM). It was also named an Overall Leader in the 2025 KuppingerCole Leadership Compass for Enterprise Secrets Management. [9]
7. Duo Security

Number of clients: 100,000+
Core Rivalry: MFA, SSO, & Zero Trust solution
Competitive Edge: Rapid deployment, Granular access policies
Duo Security offers a simple, cloud-based security platform that makes it easy for IT teams to protect applications, devices, and users from unauthorized access. Its tagline, “Democratizing security,” reflects its philosophy of user-friendly, accessible, and scalable protection.
It gained widespread popularity due to its clean interface, low-friction mobile push authentication, and broad integrations with applications such as Microsoft 365, Salesforce, and AWS.
In 2018, it was acquired by Cisco Systems for approximately $2.35 billion. Since then, it has become a core component of Cisco’s broader security strategy, playing a key role within the Cisco Secure Access and Cisco Zero Trust frameworks. [10]
Duo is frequently highlighted for delivering a 159% ROI, showing productivity gains and reduced helpdesk burden for customers deploying MFA and Zero Trust access controls. A case study with Cisco itself reveals deployment across 100,000 users and 170,000 devices, securing over 5 million access attempts per month.
As of today, the platform protects over 100,000 organizations worldwide and processes over 1 billion authentication events monthly.
6. Amazon Cognito
Launched: 2014Scale: 100 billion+ authentications per month
Core Rivalry: Competes in CIAM for AWS-native apps
Competitive Edge: Tight AWS integration, cost-effective for startups
Amazon Cognito is a user authentication, authorization, and user management service developed by Amazon Web Services (AWS). It was developed to streamline the identity experience for developers building mobile and web applications.
It supports both federated identity providers like Google and Facebook as well as SAML-based enterprise identity providers such as Okta. This makes it a flexible solution for apps targeting both consumer and enterprise users.
Cognito supports many advanced security features including adaptive risk-based authentication, compromised credential detection, IP geolocation velocity tracking, and customizable authentication flows triggered via AWS Lambda. It also enables passwordless login using FIDO2-based passkeys, SMS or email OTP requested via hosted UI or custom UI.
The platform processes over 100 billion authentications per month, scaling seamlessly to millions of users through user pools and identity federation with SAML, OpenID Connect, and social identity providers.
5. Google Identity Platform
Launched: 2022Core Rivalry: Developer-first CIAM and federated login
Competitive Edge: Native Google ecosystem integration, OAuth/OpenID standards leadership
Google Identity Platform serves as a foundational layer for securely managing users, authentication, and access control across web, mobile, and enterprise applications.
It was originally built to support Google’s internal infrastructure and products like Gmail and YouTube, but later evolved into a robust, developer-friendly identity-as-a-service (IDaaS) solution available to third-party apps and organizations.
At the core of this platform is Firebase Authentication, designed for developers who need fast, secure, and easy user authentication across mobile and web apps. Firebase Auth supports major identity providers including Google, Facebook, Apple, GitHub, Twitter, and Microsoft, as well as traditional email/password logins and phone number verifications.
To detect anomalies (like suspicious IPs or new device logins), Identity Platform leverages Google’s AI/ML models, similar to risk-based identity management seen in zero-trust solutions.
The platform supports tens of millions of users, thanks to its planet-scale reliability and SLA-backed uptime (99.95%). According to PeerSpot data, Google Cloud Identity Platform holds approximately 10.9% of the IAM-as-a-Service market mindshare, ranking second only to Okta Workforce Identity at 12.1%. [11][12]
4. SailPoint
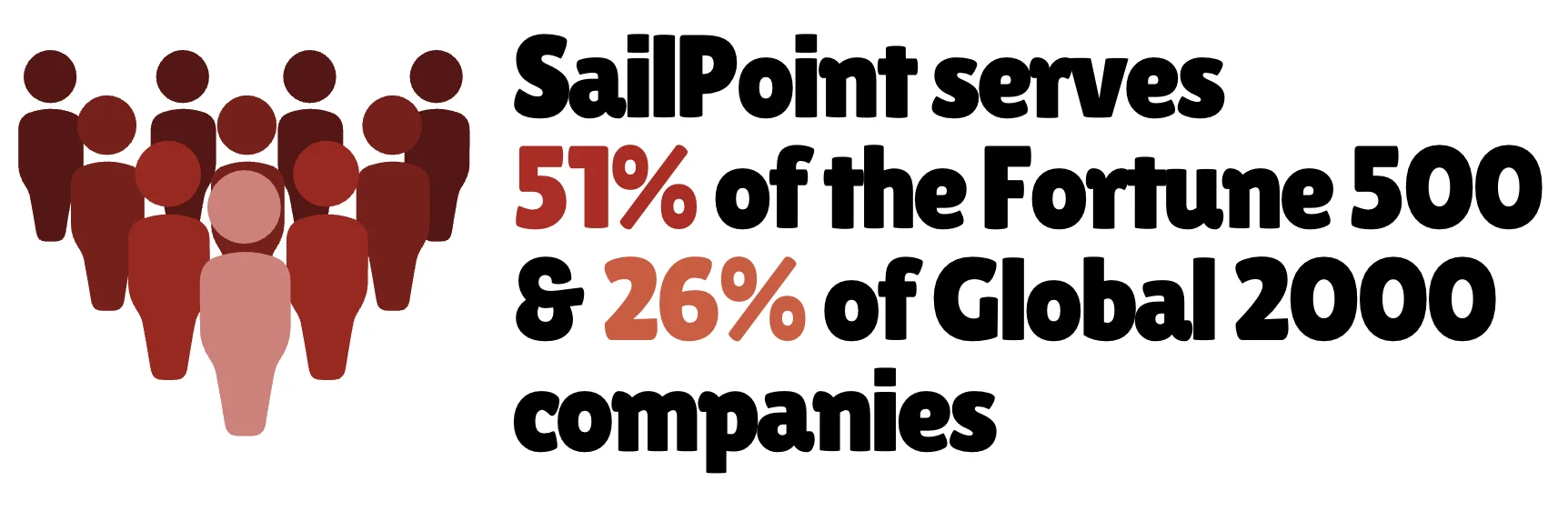
Revenue: $925 million+
Core Rivalry: Strong in IGA
Competitive Edge: High customer trust and retention
SailPoint’s emphasis on AI-driven insights puts it at the forefront of Identity Governance and Administration (IGA) evolution. Its flagship platform, IdentityIQ, was one of the first to bring comprehensive access certification, role management, and policy enforcement into large enterprises.
Another key offering, IdentityNow, is a cloud-native, SaaS-based IGA suite that provides faster time-to-value and reduced maintenance compared to traditional on-premise deployments. IdentityNow supports a range of use cases including user provisioning, access requests, access reviews, and compliance reporting, all delivered through a multi-tenant architecture.
Compared to Okta, SailPoint excels in scenarios where audit readiness, segregation of duties, and continuous compliance are paramount, particularly in regulated industries. While Okta’s modular governance features may suffice for basic attestation, SailPoint’s depth of analytics and third‑party oversight is unmatched.
Over the past decade, SailPoint’s platform has been widely adopted by some of the world’s largest enterprises, particularly in the financial services, healthcare, and public sectors, where governance, auditability, and risk mitigation are non‑negotiable.
In FY 2025, SailPoint reported a 30% increase in annual recurring revenue (ARR), reaching $925 million, while its SaaS ARR rose by 39% to $574 million. A major driver of this growth has been enterprise expansion; customers generating over $1 million ARR surged ~62% YoY . [13]
3. IBM Security Verify
Rebranded: 2020Number of users: 27 million+
Core Rivalry: Complex IAM deployments in regulated sectors
Competitive Edge: Massive scalability and reliability
As a part of IBM’s broader security portfolio, Security Verify is designed to serve large organizations with hybrid or multi-cloud architectures.
The platform provides a comprehensive set of IAM capabilities, including single sign-on (SSO), multifactor authentication (MFA), identity governance and administration (IGA), risk-based access, privileged access management (PAM) integrations, and consumer identity and access management (CIAM).
It utilizes AI and analytics to continuously assess identity risks, user behavior anomalies, and access violations — all while providing actionable insights to administrators.
As part of IBM’s Zero Trust framework, Security Verify integrates seamlessly with other IBM Security products like Guardium, QRadar, and IBM Cloud Pak for Security. It also supports deep integrations with enterprise directories (like Microsoft Active Directory), HR systems, and third-party applications through RESTful APIs and open standards (SAML, OIDC, SCIM).
The platform secures over 27 million internal and external identities, handling more than 35 million logins each quarter across 5,000 applications, over 600 federated client organizations, and 150,000 authorization groups. [14]
2. Ping Identity

Number of Accounts: 8 billion+
Core Rivalry: Competes directly in hybrid IAM & CIAM
Competitive Edge: Enterprise-grade customization, deployment flexibility
Ping Identity targets mid-sized to large enterprises, including many Global 2000 organizations, helping them securely manage employee, partner, and customer access to applications and services.
It supports complex identity and access management (IAM) requirements through standards-based federation, single sign-on (SSO), multi-factor authentication (MFA), directory services, and API security.
One of Ping’s greatest strengths lies in its interoperability: it enables seamless integration with existing infrastructure like Active Directory and cloud platforms (AWS, Azure, Google Cloud).
The company has also invested in adaptive authentication and AI-driven access intelligence to balance user experience and security. Its risk-based decision engine analyzes factors such as device reputation, user behavior, and geolocation in real time, enabling it to grant or restrict access dynamically.
In FY 2024, the company reported a 31% year-over-year increase in annual recurring revenue (ARR), surpassing the $800 million milestone in its SaaS portfolio. It now secures over 8 billion accounts worldwide, serving customers that include more than half of the Fortune 100. [15]
According to Gartner’s Critical Capabilities report for Access Management 2025, Ping scored the highest across all five IAM use cases: Customer, Workforce, Partner (B2B), Application Development, and Machine Identity. [16]
1. Microsoft Entra ID

Number of Clients: 720,000+
Core Rivalry: Challenges Okta in enterprise SSO & cloud identity
Competitive Edge: Zero Trust and AI Security
Entra ID supports enterprise-level identity and access needs, including authentication, conditional access policies, role-based access control, and identity governance. This is all embedded into Microsoft’s suite of services.
Its Zero Trust architecture leverages contextual and behavioral risk signals with AI-based adaptive policies, tying into Microsoft’s massive Security Graph intelligence for real‑time threat detection.
It offers passwordless and phishing-resistant authentication, including FIDO2, Windows Hello, and native passkey support, thereby reducing reliance on traditional credentials. Plus, features like PIM, Conditional Access, and governance dashboards make it robust for compliance-driven enterprises.
As of today, Microsoft Entra ID supports billions of authentications per day, across more than 720,000 organizations.
A commissioned Forrester study found that companies using Entra (including Entra ID, Permissions Management, and Verified ID) achieved a 240% ROI over three years. These organizations realized $12.1 million in benefits versus $3.57 million in costs, with a net present value of $8.57 million. [17]
Read More
Sources Cited and Additional References- Businesses at Work, A new era demands new tools, Okta
- Information Technology, IAM market size and trend analysis, Skyquest
- Ali Adib, Organizations need modern passwordless authentication to stop data breaches, RSA
- Cloud Platform, Administering Oracle Identity Cloud Service. Oracle
- HID, 2025 Security report highlights AI and mobile innovation, SourceSecurity
- Markets, Cybersecurity company CyberArk to acquire Venafi in $1.5 billion deal, Reuters
- Newsroom, CyberArk acquires Zilla Security, CyberArk
- News, Transmit Security Places in Fortune’s 2025 Cyber 60, Yahoo Finance
- BeyondTrust Corporation, An overall leader in KuppingerCole leadership compass, GlobeNewswire
- Liana Baker, Cisco to buy cyber-security company Duo for $2.35 billion, Reuters
- Identity Platform, Benefits and key features, Google Cloud
- Comparison Buyer’s Guide, Google Cloud Identity vs Okta Workforce Identity, PeerSpot
- Financial Result, Grew ARR 30% year-over-year to $925 million, SailPoint
- Case Studies, Simplifying secure identity and access for over 27 million users, IBM
- News Releases, Ping Identity surpasses 30% annual growth in SaaS revenue, PR Newswire
- Peter Barker, Ping Identity scores highest in all Gartner Critical Capabilities use cases, Ping Identity
- Forrester Study, Microsoft Entra delivers 240 percent ROI, Microsoft